DUOS expands AI capabilities to help seniors apply for assistance programs
It will complete and submit forms, and integrate with state benefit systems
Read more...
Well, here’s some news to ruin your Friday. Turns out, the NSA can get around many forms of encryption, according to newly released documents obtained by Edward Snowden. The story was published by the New York Times, the Guardian, and ProPublica—the first story to come out of the three-way partnership the news outlets formed after the British government threatened the Guardian with legal action unless it destroyed documents leaked by Snowden.
The newly released documents reveal the ways in which the NSA has undermined and possibly even “cracked” encryption, which safeguards everything from financial transactions and banking data to medical information.
It seems the agency has developed both low-tech and high-tech ways of getting around encryption in a classified program code-named Bullrun. The NSA has been able to use these methods to secure emails, Internet searches, chats, and phone calls of American citizens and others around the world.
One of the more low-tech methods involves basic collaboration with domestic and overseas tech companies to build back doors into their security codes and giving the NSA the encryption key. The documents don’t specify which companies have been targeted, but some companies have said they were coerced into building weaknesses that the NSA could exploit.
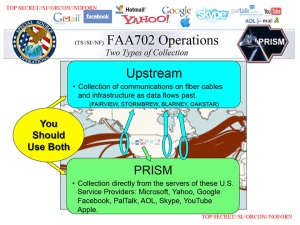
The documents do, however, say that the NSA and its British counterpart, GCHQ, have been looking into ways to infiltrate protected traffic of Google, Yahoo, Facebook, and Microsoft’s Hotmail. Google has denied giving access to any government agency and said it has no evidence of a security breach, despite the fact that the newly leaked documents describe how GCHQ claims to have developed “new access opportunities into Google’s systems.”
The agency has also developed custom-built, superfast computers capable of breaking code, which seems to imply the use of “brute force” attacks (running trillions of possible passwords per second until the right one is found). But as Geoffrey Ingersoll notes, the upper practical limit on brute force attacks is 80 bits, while the lowest level of bits on encryption is 128. And most websites are phasing out of 1024-bit keys and moving into 2048-bit keys. So a brute force attack would be unlikely to unscramble encrypted code.
So it’s highly unlikely that the NSA is actually “cracking” encrypted text. It’s more likely that “Bullrun” is operating primarily on purposely built-in weaknesses designed specifically for the NSA’s access.
Back in the 1990s, the NSA had petitioned for a government back door to all Internet encryption, known as the Clipper Chip. The agency saw a lot of backlash over the Clipper Chip as many organizations and lawmakers were concerned with the potential for unmitigated and unsupervised spying on American citizens.
Indeed, NSA agents have been found on several occasions to use the agency’s technology and resources to spy on love interests. The practice is not widespread, but it’s common enough to have its own term: LOVEINT.
The NSA spends more than $250 million a year on its efforts to influence/compel tech companies to create encryption access points for government agencies.
Yesterday, the Pew Internet Project released a study showing that 86% of U.S. Web users are concerned about online privacy and have taken steps to hide their digital footprint. Today, 50% of Internet users are worried about how much of their information is available online, which is up from 33% in 2009.
image source: takepart.com
It will complete and submit forms, and integrate with state benefit systems
Read more...The bill would require a report on how these industries use AI to valuate homes and underwrite loans
Read more...The artists wrote an open letter accusing OpenAI of misleading and using them
Read more...